What are User Access Reviews?
Discover the importance of user access reviews in data security and compliance.

For Identity and Access Management (IAM) practitioners, few tasks are as dreaded—or as critical—as user access reviews. Traditionally, this workflow involves weeks of aggregating spreadsheets, chasing down managers for approvals, and deciphering nested group permissions. It is a manual bottleneck that drains resources, invites human error, and often fails to provide true visibility into user identities across the organization.
This guide explores how to automate user access reviews to transform this chaotic ritual into a streamlined, continuous operation. We will cover the specific mechanics of how automation replaces manual aggregation, the key components required for an effective automated workflow, and best practices for implementation. We will also provide a blueprint for selling this shift to your leadership by focusing on ROI through license reclamation and risk reduction.
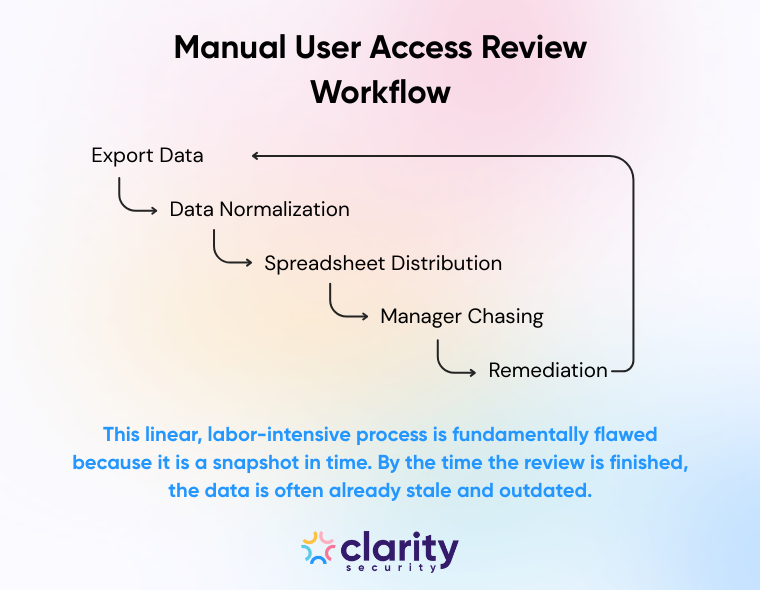
To understand the value of an automated user access review system, we first have to honestly assess the legacy method. For most security teams, the traditional workflow is disjointed and reactive. It usually looks something like this:
This linear, labor-intensive process is fundamentally flawed because it is a snapshot in time. By the time the review is finished, the data is often already stale and outdated.
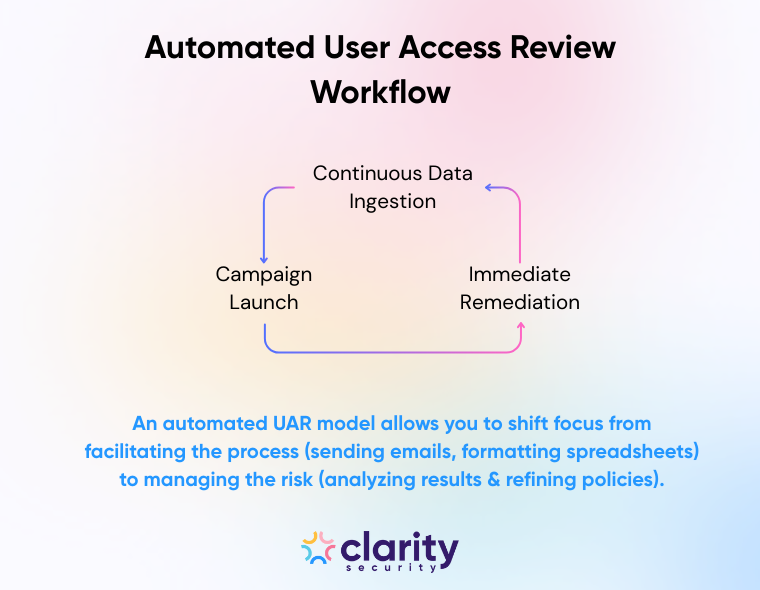
When you automate user access reviews, the workflow shifts from a linear project to a continuous cycle. Automation changes the architecture of the review in three distinct phases:
By moving to this model, IAM practitioners shift their focus from facilitating the process (sending emails, formatting sheets) to managing the risk (analyzing the results and refining policies).
The primary driver to automate user access review processes is often efficiency, but the reduction in risk is equally critical. Manual reviews are notoriously prone to rubber stamping, where managers, overwhelmed by the volume of obscure entitlement data, approve access without truly reviewing it.
In manual reviews, information is often presented without context. A manager sees a line item like CN=Finance_RW_102. They don't know what it means, so they approve it to avoid potentially disrupting their employee's work. This is the path of least resistance, but it leads to access creep, technical debt, and potential audit findings.
Ticket-heavy processes weigh down security teams. They drain resources and create unnecessary risk.
When you use an automated UAR platform, you can inject context directly into the review interface. Instead of a raw group name, the reviewer sees "Read/Write access to Financial Records." This clarity empowers the reviewer to make an informed decision, reducing the likelihood of blind approvals.
Human error is inevitable when humans act as middleware. Every time an analyst copies data from a CSV to a master sheet, there is a risk of misalignment. Every time they manually interpret a manager's email response, there is a risk of misunderstanding.
Automated systems normalize identity data from any source—CSV, API, SCIM, SAML—transforming it into a unified format without human intervention. This ensures that the data being reviewed is accurate.
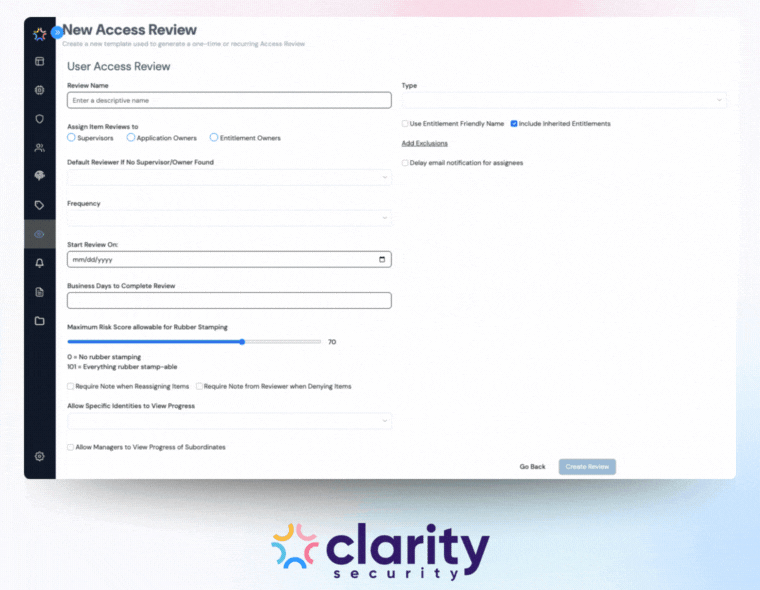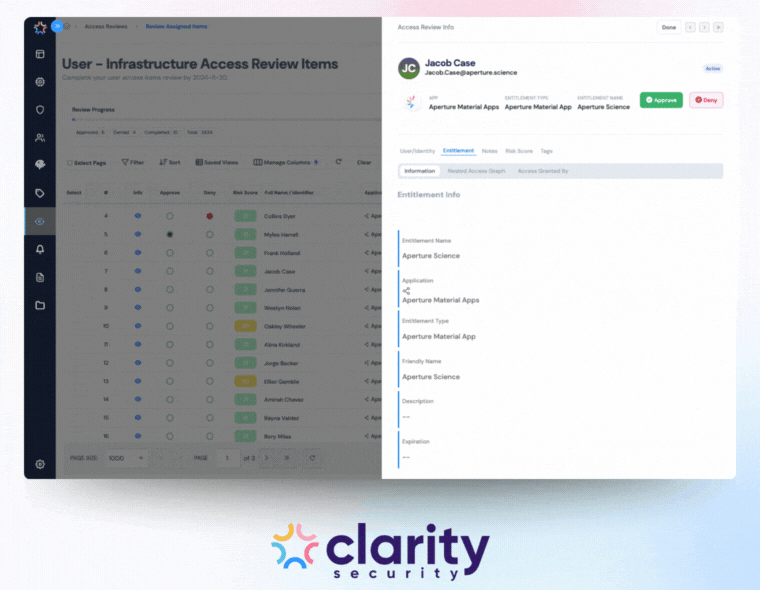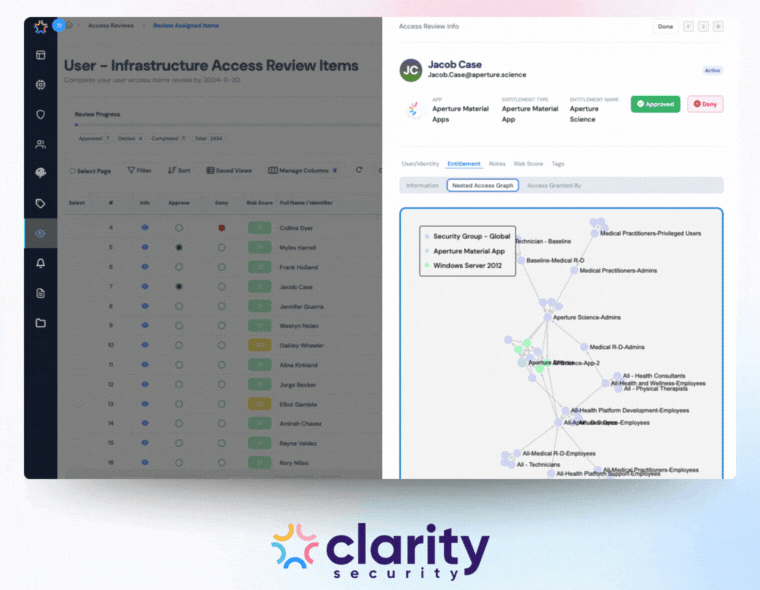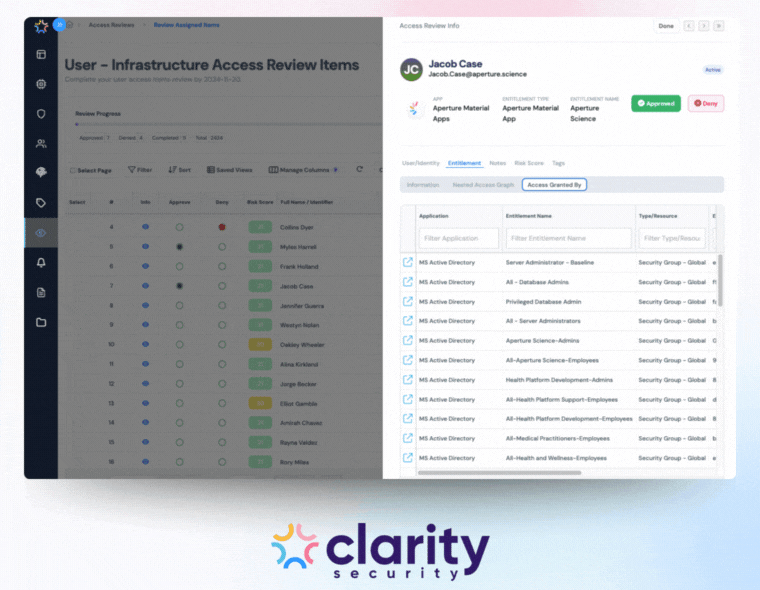
Furthermore, automated systems can handle nested access resolution, automatically untangling complex group nestings to show the effective permissions a user actually possesses. This visibility is nearly impossible to achieve manually at scale.
Manual reviews often happen quarterly or annually. In the months between reviews, users may accumulate high-risk permissions that violate compliance policies.
Automated systems provide continuous monitoring and cleanup. They can detect access drift in real-time and alert the IAM team or trigger a remediation workflow immediately. This means errors are caught in minutes, not months.
To successfully automate user access review cycles, your solution or build-out needs specific technical capabilities. Digitizing the spreadsheet is not enough; the system must understand the identity context.
You cannot govern what you cannot see. An effective system must manage user identities, both human and non-human, across cloud, hybrid, and on-prem environments in one platform. It needs to ingest data from:
Many legacy systems rely solely on role-based access control (RBAC), which often leads to role explosion and maintenance headaches. An ABAC engine allows you to dynamically grant or revoke access based on real-time attributes like job title, location, or department.
In the context of reviews, ABAC-powered lifecycle management can pre-approve birthright access (access everyone in a department should have), allowing managers to focus their review only on exceptional or high-risk access. This significantly reduces review fatigue.
The system must be able to calculate effective permissions. It should see exactly what any identity can do, including inherited and group-based permissions.
For example, let's say a user is in Group A. Group A is nested in Group B. Group B has admin rights, which will then give all users in Group A admin rights as well. An automated platform can show you these nested entitlements to ensure accuracy. This also provides reviewers with context to know how a specific user gained access to an application.
The loop must be closed automatically. The system requires workflow orchestration capabilities to provision and deprovision access without manual ticketing. This includes retry logic—if a target system is down when a revoke command is sent, the system should queue the request and retry until successful, ensuring audit compliance.
Finally, the system must automatically generate a paper trail. It should produce attribute-level audit trails showing exactly who had access, who reviewed it, when they reviewed it, and what action was taken. This capability transforms the audit from a scramble for evidence into a click-to-fulfill request for compliance reports.
Implementing automation is as much about process design as it is about technology. Here are best practices for IAM practitioners looking to automate user access review workflows effectively.

Do not try to boil the ocean. You do not need to review every birthright access entitlement every quarter. Use a risk-based approach:
Move away from calendar-based reviews where possible. Implement micro-certifications triggered by lifecycle events:
Ensure your automated notifications and portals speak the language of the business, not the database.
Automation speeds up processes; if your process is bad, you will just mess things up faster. Before turning on full automation, use the system’s visibility to identify and remove orphan accounts (accounts with no owner) and toxic combinations (Separation of Duties violations).
You likely already understand the operational benefits of automation. You feel the pain of the spreadsheets and the angry emails from managers. However, convincing a CISO, VP, or CFO to invest in a new platform requires speaking their language.
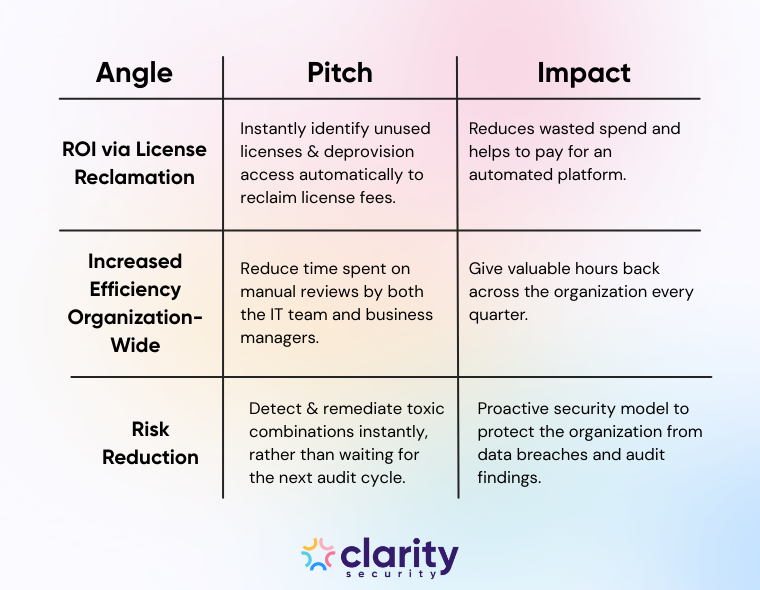
To get buy-in, you must shift the conversation from "making my job easier" to "saving the company money and reducing liability." Here are three pillars to build your business case around.
One of the fastest ways to justify the cost of an identity governance platform is through license reclamation. In many organizations, SaaS spend is bloated not just by active employees who don’t use the tools, but by orphaned accounts - licenses attached to terminated employees, ex-contractors, or service accounts that were never fully deprovisioned.
Manual reviews rarely catch this because managers 1) approve access to avoid disruption and 2) spreadsheets are static and disconnected from the HRIS.
An automated platform integrated across your entire environment can instantly identify users who not only haven’t logged in, but also find accounts that don’t have a valid owner in the directory.
The Pitch: "We are likely paying for licenses for people who no longer work here. By automating our reviews and lifecycle management, we can identify and automatically reclaim both unused licenses and orphaned accounts. If we reclaim just 10% of our SaaS stack, the platform pays for itself within the first year."
The Impact: This frees up expensive SaaS licenses immediately, reducing wasted spend and delaying the need to purchase additional seats.
Leadership wants to know that their teams are working on strategic initiatives, not administrative overhead. Manual reviews act as a massive tax on productivity—not just for the security team, but for every manager in the company who has to trudge through a spreadsheet.
The Pitch: "Currently, our team spends X hours per quarter manually prepping data for audits. Automating this process will reduce review prep time by up to 80%. Furthermore, by providing a cleaner, faster experience for business managers, we give hundreds of hours of productivity back to the organization annually."
The Impact: This transforms the security team into an organization-wide enabler. Plus, the security team has hours back in their day to focus on more strategic initiatives rather than spreadsheet maintenance and manual provisioning tickets.
The ultimate currency for a CISO is risk. Manual reviews are prone to human error, leaving high-risk permissions active long after they should have been revoked. Orphaned accounts (accounts with no active owner) are a primary vector for bad actors.
The Pitch: "Our current manual snapshot approach leaves us vulnerable to access drift for months at a time. Automation provides continuous monitoring. We can detect and remediate toxic combinations or orphaned accounts instantly, rather than waiting for the next audit cycle."
The Impact: This proactive stance protects the organization’s brand reputation and prevents costly fines associated with failed compliance reports or data breaches.
By framing the investment in terms of license reclamation, operational efficiency, and quantifiable risk reduction, you position the platform not as a tool for the security team, but as a strategic asset for the entire enterprise.
At Clarity Security, we understand that security teams are weighed down by manual, ticket-heavy identity governance processes. We exist to change that. We replace the chaos of manual processes with autonomous identity governance, removing complexity and ticket fatigue.
For the IAM practitioner, Clarity serves as a force multiplier. We don’t just provide a tool for sending emails; we provide a platform for autonomous access reviews.
Clarity ingests, transforms, and unifies data from any source—CSV, API, SCIM, SAML—giving security teams clean, actionable insights. We handle the heavy lifting of data aggregation so you don't have to.
We enable you to run context-rich certifications in minutes. Our platform utilizes Attribute-Based Access Control (ABAC) to intelligently highlight high-risk permissions. We present reviewers with clear, human-readable data, allowing them to make accurate decisions without the guesswork.
Clarity offers one-click cleanup and provisioning. When a reviewer revokes access, Clarity instantly removes permissions or accounts without manual ticketing. We orchestrate the deprovisioning flow, ensuring that the change is reflected in the target system immediately.
Beyond the review cycle, Clarity provides real-time drift detection. We continuously monitor for deviations from your "gold standard" access models and trigger alerts or remediation workflows when identities no longer match their intended profiles.
By automating the review cycle, Clarity helps you reclaim hundreds of operational hours. We help you transform from a bottleneck into a business enabler, allowing you to focus on strategic security initiatives rather than spreadsheet maintenance.
To automate user access review processes is to reclaim your time and sanity. It is about moving from "checking the box" to actually securing the environment. Clarity Security provides the intelligence, speed, and simplicity required to make this transition effortless.
Ready to eliminate ticket fatigue and automate your access reviews? Request a Demo with our team today!
Discover the importance of user access reviews in data security and compliance.
User access reviews typically comes with some pretty notable downsides. Learn how Clarity Security can enhance your security and compliance.
Managers rubberstamp User Access Reviews for a number of reasons. Regardless of what's causing rubberstamping, it's important to get this practice...
Be the first to know about new Identity Governance insights, cybersecurity industry news, and product updates.