In a world where cybersecurity regulations are getting more and more stringent, audits are essentially unavoidable. This could be for a variety of reasons. Maybe you are working for a public company, or in a regulated industry, or maybe your company just has sensitive customers… Regardless of how you fell into regulatory compliance requirements, you’re beholden to them now. Stuck forever in a loop of tedious audit tasks.. Or are you?
To understand the ground you find yourself on and what options you are looking at, there is one key question you need to be able to answer: Can you maintain what you already have, or do you need to go evaluate solutions to solve pain points you can’t live with? And, it is, unfortunately, a question that can be rather hard to answer.
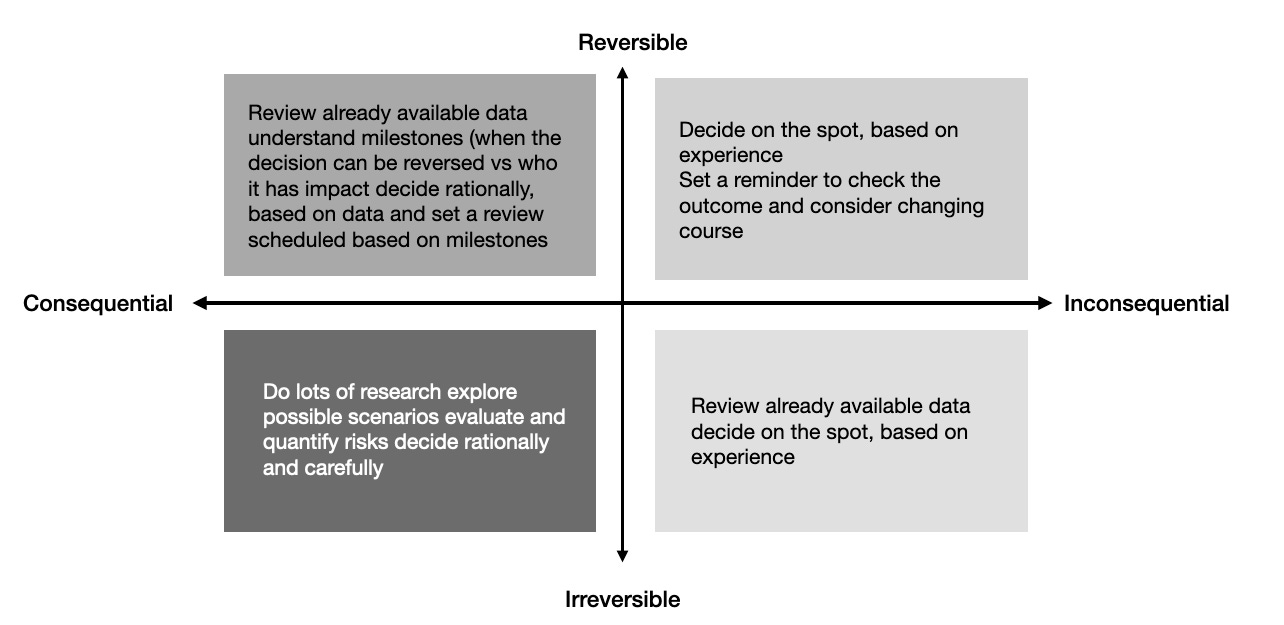
To promote an organized, simplified way of solving this riddle, your best bet is to leverage a clear and structured framework to assess how you think about IGA initiatives. To do this, define the requirements, the goals, and the long term cost of the decision. (We are huge fans of Jeff Bezos’s decision-making system, applied to IGA.)
Are you creating IGA Building Blocks?
When organizations are starting out with IGA strategies, they typically follow a structured approach to ensure the effective management of identities and access within their systems.
Here are the top eight questions to ask to best understand where your identity governance program is right now and whether you’ve got the fundamentals covered:
- Do you have a good assessment of current state?
This involves understanding existing processes, technologies, and challenges related to user provisioning, access management, compliance, and security.
- Have you defined objectives and requirements?
This includes improving security, streamlining access request processes, ensuring compliance with regulations, and reducing the risk of insider threats.
- How would you select an IGA solution? What are your must haves? What are your nice to haves?
This encompasses researching available solutions, conducting vendor evaluations, and considering factors such as scalability, integration capabilities, compliance features, and cost based on defined requirements.
- Who is going to own the work? Who’s fault is it if something goes wrong?
This means defining roles and responsibilities, workflows for user provisioning and access requests, policies for access control and segregation of duties (SoD), and integration with existing systems.
- Do you have the ability to implement, integrate, and implement some more?
Integration with other systems and applications includes deploying connectors or agents to synchronize user data, configuring access policies, and setting up workflows for access request and approval. This can be challenging for teams if the right internal resources aren’t available or don’t have the right skills.
- How do you validate your system is correct?
Testing and solving for process inaccuracies in the user provisioning and deprovisioning processes, access control mechanisms, compliance reporting, and user experience once your IGA solution is already built-out and in motion can be a VERY hard problem to solve. Again, resources and team skill sets are key.
- Can you manage training costs and change management?
Training sessions are a non-negotiable way to familiarize employees with identity governance processes and tools. Additionally, change management is a forever problem. And while it is a normal issue to have, it can be a much larger source of frustration if you are also maintaining a home-grown solution.
- Can you continuously improve?
Running your audit is hard enough on its own, but can you afford to continue to invest in new systems, tooling, and process improvements? It’s crucial to make sure you are provided both the headcount and funding for maintaining what you build. Owning it doesn’t mean it’s free.
Going through the practice of answering these questions enables organizations to establish a solid understanding of their current capacity and limitations for managing identities and access effectively through their IGA strategies.
Build or Buy?
Now that you know both what the pain points in your current process are and the requirements of where you need to go, there's one question that determines if the next year is one of pain and suffering, or champagne and caviar: Do you have the right budget for what you need? Choosing to build or buy is going to cost you no matter which direction you choose to go.Therefore, it’s pertinent that you ensure you have the manpower and budget to do a good job, or a material deficiency is in your future (just ask some of our customers).
Here are a few more important points of consideration when debating which route is best for your organization:
- Do you have any single points of failure in terms of technical skills?
Can you identify any one individual whose departure would wreak havoc on your ability to maintain your identity governance initiatives? If so, can you afford to proactively hire a second person as their backup in the event they leave your company? If the answer is no, maintaining and relying on an in-house solution may set you up for a high-key stressful situation later.
- Do you need something better than excel, or do you have broad ranging digital transformation initiatives?
Just because a company offers a bazillion solutions, doesn’t mean that you need them all. Sometimes “easier than excel” is a great answer. Vice versa, be mindful not to buy things you DON’T need as well.
- Do you really need the headache, or would you rather call someone and let them solve it?
Your strategic value to your company is NOT delivering an in-house IGA solution. While it’s true that you must deliver a clean audit, the opportunity cost of over-investing in one area of your security infrastructure can be high. Focus on what creates the most value for the business, and consider outsourcing the rest.
- Who’s your compliance expert?
Remember, security and regulatory landscapes are constantly changing. GDPR was released in 2016 and transformed digital marketing. NIST is constantly receiving updates. Someone on your team has to actually read all that stuff, which is not only gross (Unless you're security nerds like us!), but also extremely time-consuming.
How Clarity Can Help
Clarity is built for security professionals as the easiest way to complete your audits.
Clarity's platform provides a powerful integration framework (that allows you to get all the in-scope application data loaded), a simple UX for access certifications, automation to reduce manual tickets over-burdened IT teams, and compliance reporting to keep auditors happy, fed and watered. Keep it simple, keep it easy.
Schedule a demo now to learn more about how Clarity's solution can help your organization.
